I will be explaining the simplest and easiest way to configure Microsoft Defender for Identity requirements. In this guide, I will help you maximize your identity security by explaining in detail the steps to enable and configure Microsoft Defender. With easy-to-understand steps and practical tips, you can quickly set up Microsoft Defender to protect your system and data. This will save you time while increasing your security.
Test-MdiReadiness
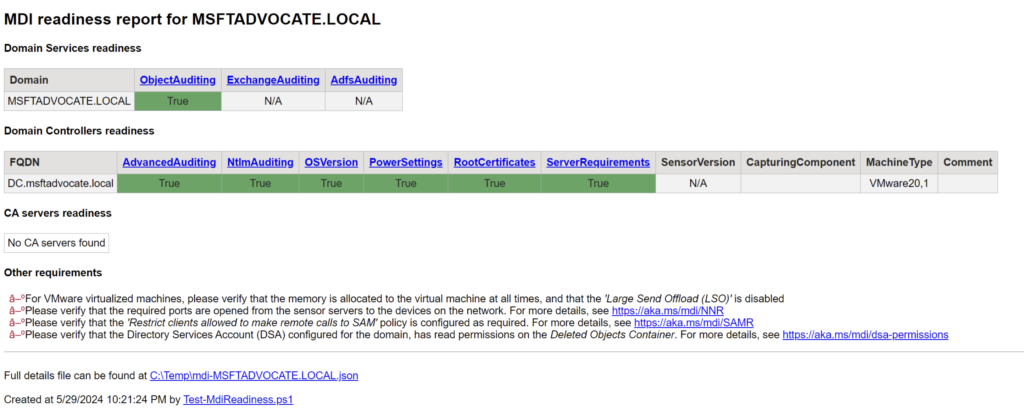
We run our Test-MdiReadiness script as follows.
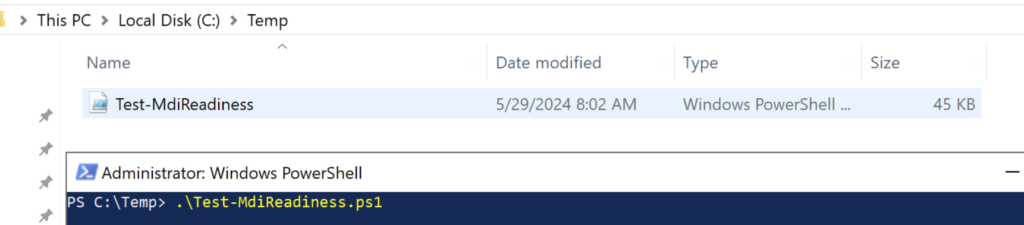
The result output will be as follows.
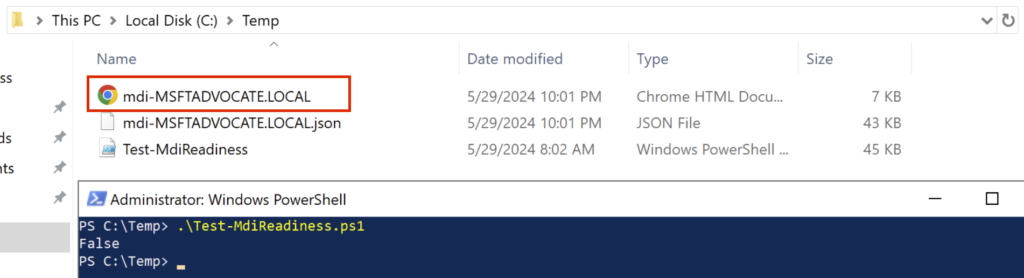
When we open the report, it shows us the shortcomings below.
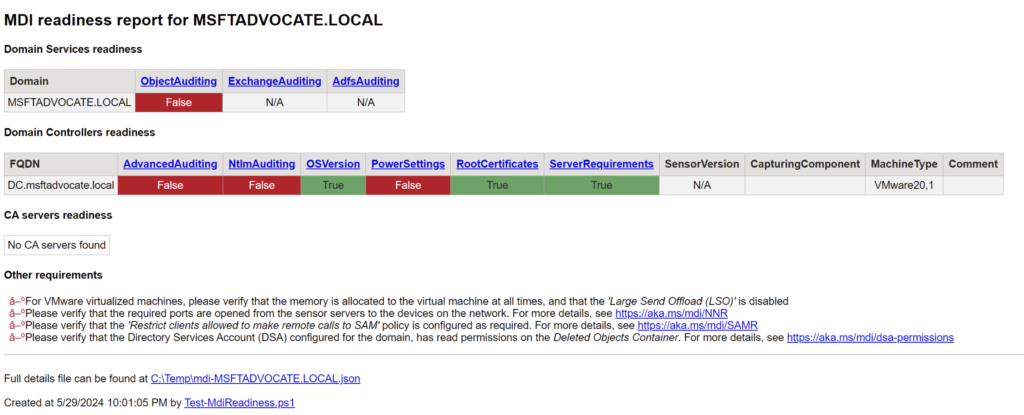
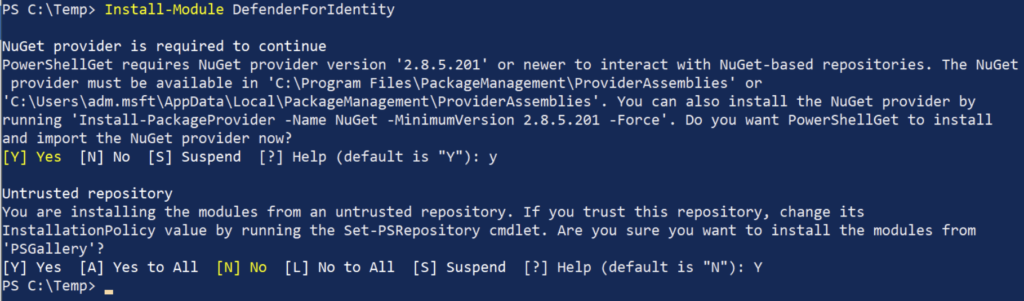
We will be using the DefenderForIdentity module to fix the reds. We load the relevant module with the following powershell command.
Install-Module DefenderForIdentity
Reporting
In my test environment, my Active Directory server takes the AD DS role. MDI requires custom configuration for each role to track activities correctly. Therefore, I will use the New-MDIConfigurationReport command to generate an HTML report of the MDI configuration for AD DS.
New-MDIConfigurationReport -Path C:\Temp -OpenHtmlReport
It outputs the directory we specified.
Our report details what happened and shows how we can fix it.
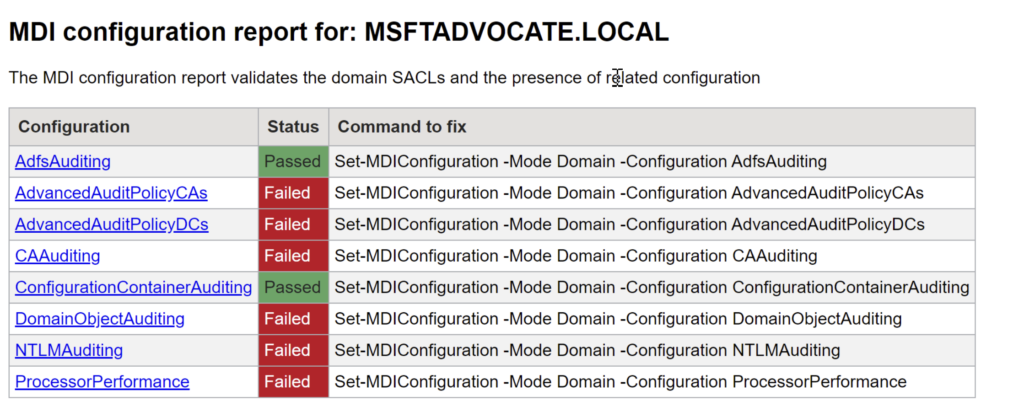
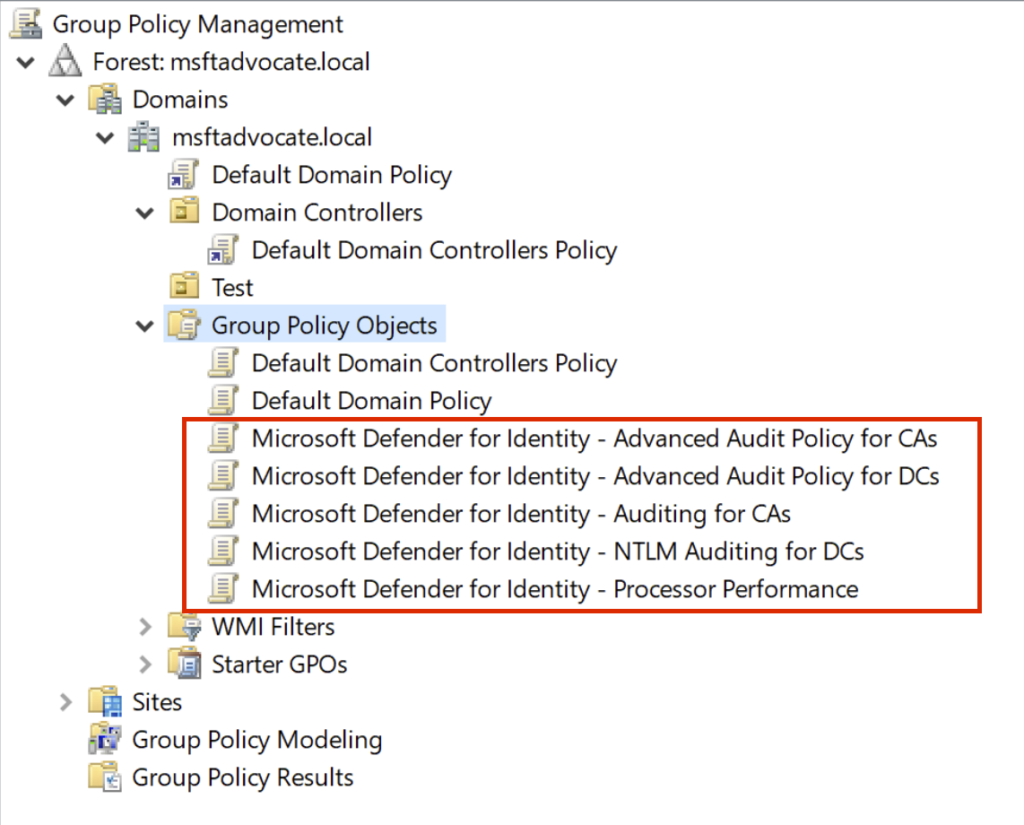
The HTML report shows that some configurations are met and some are not. Some settings required for MDI configuration are Failed. However, the good thing is that in the past, as an MDI administrator, we had to manually create the necessary GPOs for MDI. Thanks to the report command, we no longer have this hassle! Before we apply the fixes, below you can see the current GPO settings applied in my domain. We will come back to this later.
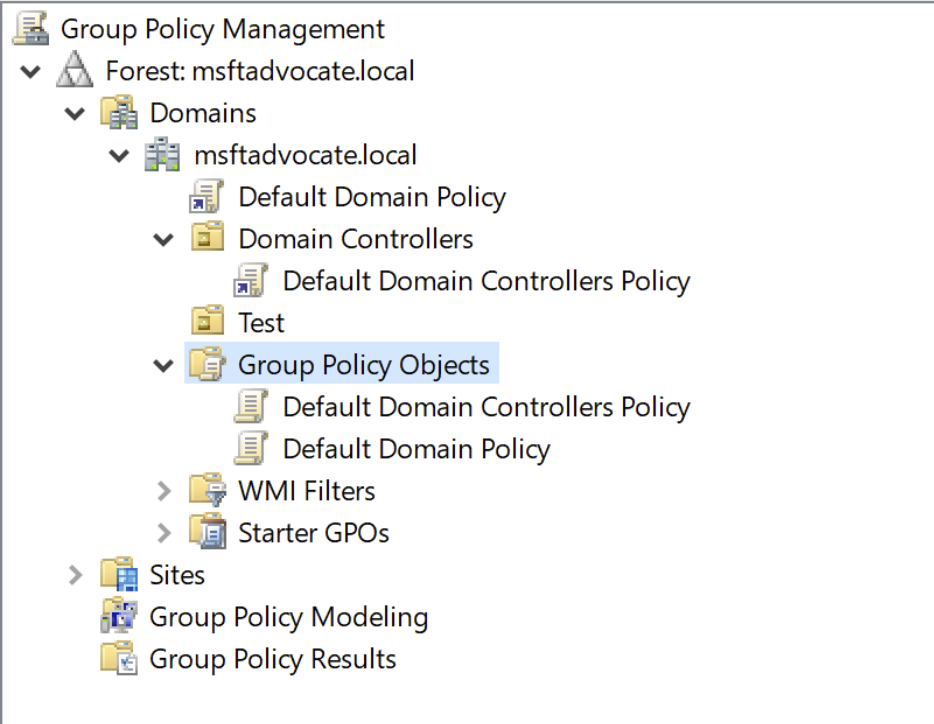
Implementation of Corrections
The HTML report lists some configurations that failed and all the commands that need to be fixed. Now let’s apply these commands to the Active Directory server and then regenerate the report.
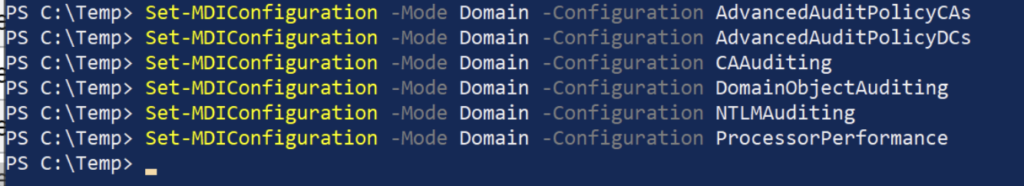
Now, after applying all the fixes listed in the HTML report, it’s time to regenerate the report and verify that all configurations are now in Passed status. For this, run the following command in PowerShell.
New-MDIConfigurationReport -Path C:\Temp -OpenHtmlReport
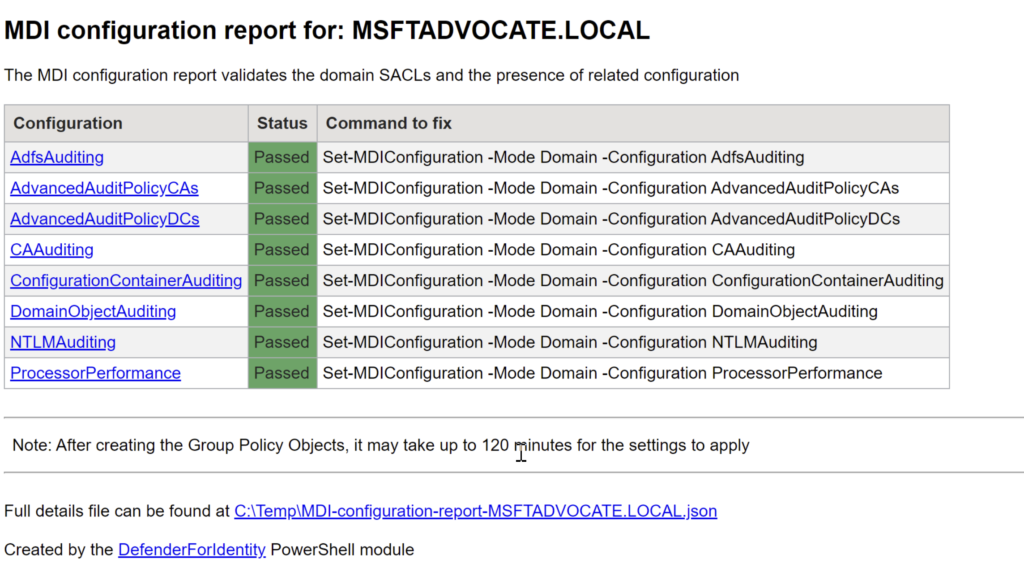
We run our Test-MdiReadiness script as follows.
Now, let’s analyze the GPOs that are active in my domain.
References
https://github.com/microsoft/Microsoft-Defender-for-Identity/tree/main/Test-MdiReadiness


