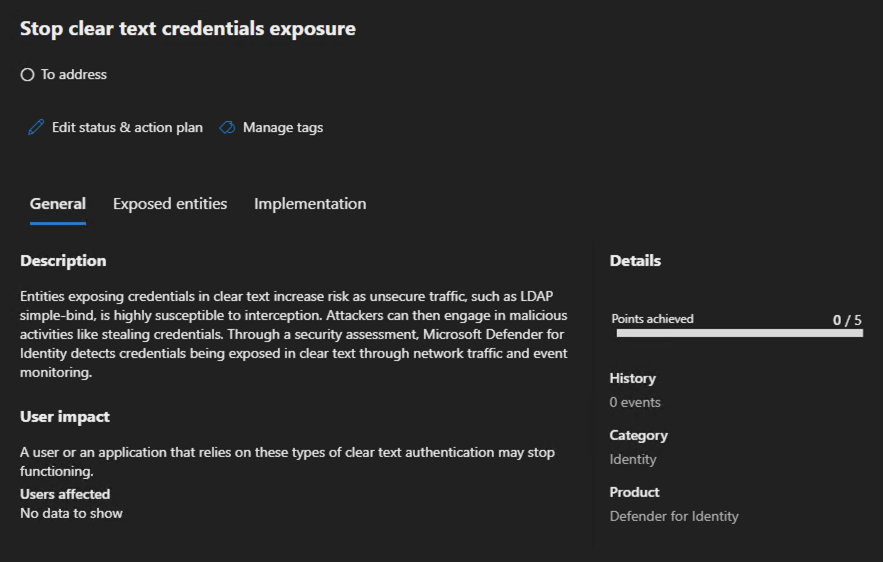
Entities exposing credentials in clear text increase risk as unsecure traffic, such as LDAP simple-bind, is highly susceptible to interception. Attackers can then engage in malicious activities like stealing credentials. Through a security assessment, Microsoft Defender for Identity detects credentials being exposed in clear text through network traffic and event monitoring.
User impact
A user or an application that relies on these types of clear text authentication may stop functioning.
LDAP Bind Operation
For authentication in Active Directory, clients use a Bind operation. The most common method of Bind is Simple Bind. With Simple Bind, the client authenticates anonymously or with the user’s Distinguished Name and password. However, Simple Bind sends the password over the network in plain text. This is vulnerable to man-in-the-middle attacks and malicious actors can easily intercept the password.
Here is an example of Simple Bind authentication in Wireshark showing the plain text password.
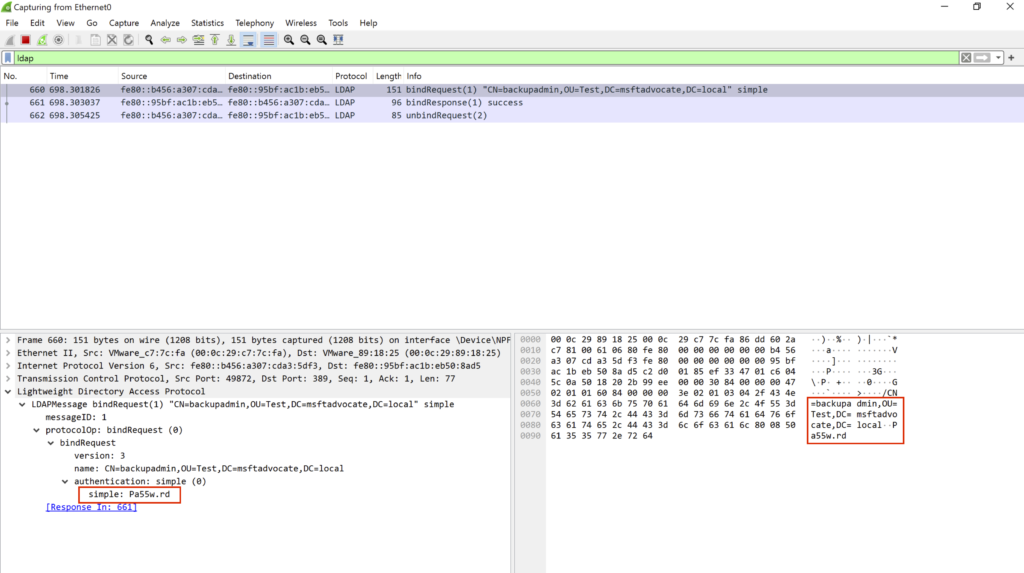
The password sent for authentication is in clear text and not encrypted.
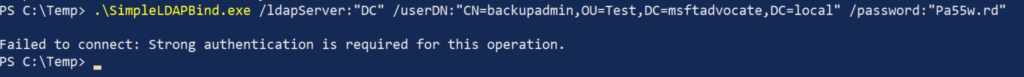
Simple LDAP Bind Tool
With Wireshark, it is possible to test the “Prevent disclosure of clear text credentials” measure and check the plaintext password with the same tool we used to do the Simple LDAP Binding.
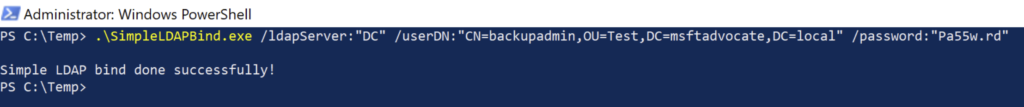
Performing a Simple LDAP Bind results in “Exposed entities” in Microsoft Defender for Identity Recommended Actions “Stop clear text credentials exposure.“
Conclusion
We edit and activate the domain controller policy as follows.
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
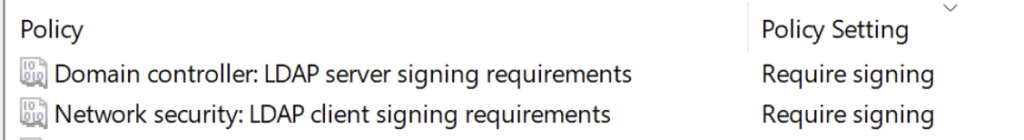
Let’s perform our post-processing test
References
https://github.com/thalpius/Microsoft-Defender-for-Identity-Simple-LDAP-Bind


